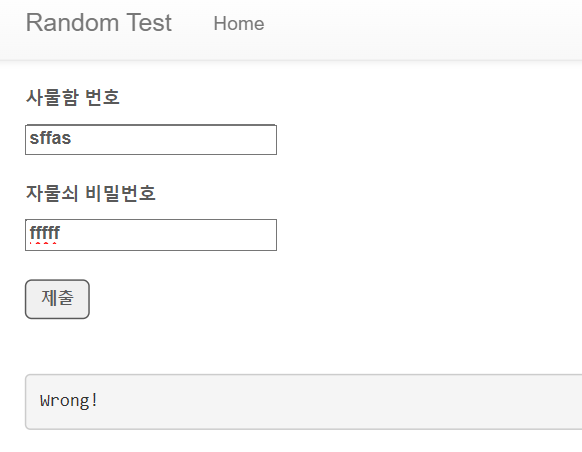
이런식으로 사물함이랑 자물쇠 비번을 맞춰야하는 문제이다 사물함 번호는 알파벳 소문자 혹은 숫자를 포함하는 4자리 랜덤 문자열이고, 비밀번호는 100 이상 200 이하의 랜덤 정수라고 한다 #!/usr/bin/python3 from flask import Flask, request, render_template import string import random app = Flask(__name__) try: FLAG = open("./flag.txt", "r").read() # flag is here! except: FLAG = "[**FLAG**]" rand_str = "" alphanumeric = string.ascii_lowercase + string.digits #소문자 or 숫자 for i in..
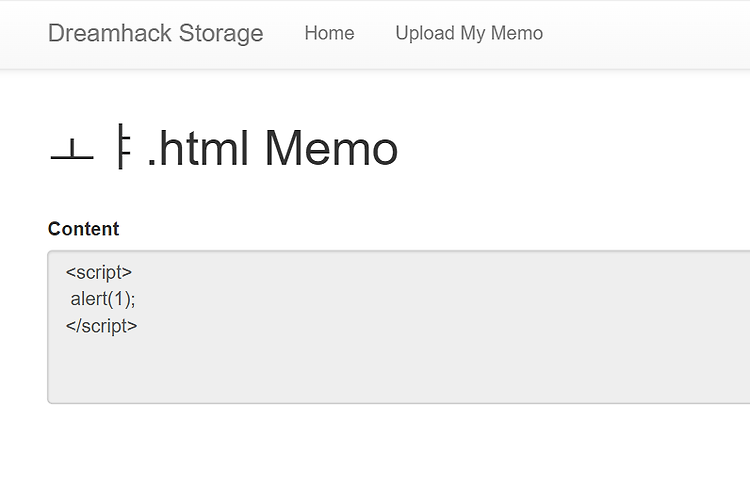
스크립트 파일을 입력을 했더니 실행이 되지 않았다. 이와 같은 태그는 우회하고 있나보다 이런식으로 path traversal을 시도해보았는데 안되었다 코드가 어떻게 이루어져있는지 이제 뜯어보도록 하겠다 #!/usr/bin/env python3 import os import shutil from flask import Flask, request, render_template, redirect from flag import FLAG APP = Flask(__name__) UPLOAD_DIR = 'uploads' @APP.route('/') def index(): files = os.listdir(UPLOAD_DIR) return render_template('index.html', files=files) @..
list.php Image Storage Home List Upload
@app.route("/flag", methods=["GET", "POST"]) def flag(): if request.method == "GET": return render_template("flag.html") elif request.method == "POST": param = request.form.get("param") form에서 param을 param으로 저장 if not check_xss(param, {"name": "flag", "value": FLAG.strip()}): return '' return '' 여기서 check_xss(param, {"name": "flag", "value": FLAG.strip()}) 호출 param은 우리가 flag에서 form으로 입력한 인자. @ap..

오늘은 버프스위트의 cluster bomb 기능을 대충 요약한 글이다. 주저리 많음ㅎㅎ ㅠ Burp Suite의 Intruder를 이용해 Blind SQL Injection을 진행하던 도중 변수 2개에 대해 각기 다른 규칙을 적용해주어야하는 일이 있었다. 나는 바보같이......... Cluster Bomb이라는 멋진 아이가 있는 줄도 모르고 ...... 수동으로 공격을 진행했다....... 위 글에 따르면 "This attack iterates through a different payload set for each defined position. The Cluster Bomb Attack is useful where an attack requires unrelated or unknown input t..